Modern IT and other enterprises are heavily dependent on servers, databases, network devices, security infrastructure and other software applications for their day-to-day operations. These infrastructure are accessed and controlled through administrative passwords. Typically, the applications are used in a shared environment by a group of administrators.
The number of administrative passwords keep on growing as more and more servers, devices and applications are added to the enterprise. Administrators end up virtually struggling with a pile of passwords and face problems on securely storing, managing and sharing the passwords. Spreadsheets, flat files and even print-outs containing the passwords are circulated among the administrators.
This traditional practice brings with it a host of issues such as the following:
- When one administrator changes a password, it should be updated in all the 'copies'; otherwise, at the most needed time, one would be trying to login with an outdated or old password!
- Chances of security attacks on the IT infrastructure become very bright
- The business of the enterprise would be in jeopardy as sensitive passwords remain insecure
In most of the organizations, a common administrative account is created and all the administrators use the same account to access the infrastructure - for instance 'Administrator' on Windows, 'root' on Unix/Linux, 'enable' on Cisco, 'sa' on SQL server etc.
These administrative passwords, also known as 'Shared Administrative Passwords' give unlimited access to the infrastructure to the extent that the user can do virtually anything. This practice brings along with it accountability issues since the super-user is not role-based and actions could not be traced back to a particular user.
According to a research report of Gartner, the shared accounts with superuser privileges or other high-level access rights pose a significant risk in all organizations. Passwords are shared by multiple users who are sanctioned to use those accounts, or they're managed using fragile manual processes. High risks stem from passwords becoming known to others, as well as the lack of individual accountability. (Source: Gartner, Inc., "Toolkit: Password Management Tools for Shared Accounts and Service Accounts", Ant Allan, 11 January 2007).
Also, IT Managers often wish to enforce certain standard password policies - such as usage of strong passwords, curbs on usage of obvious passwords, rotating passwords at periodic intervals etc. The traditional password management lacks provision for all of these policies.
Governmental and industry regulations prescribe severe security measures for protecting passwords and require comprehensive audit records on each and every action on the passwords. In the traditional approach, there is no way to ensure compliance to such regulations.
In short, administrators of enterprises are drowning in a pile of administrative passwords and are struggling to store and manage them securely and effectively.
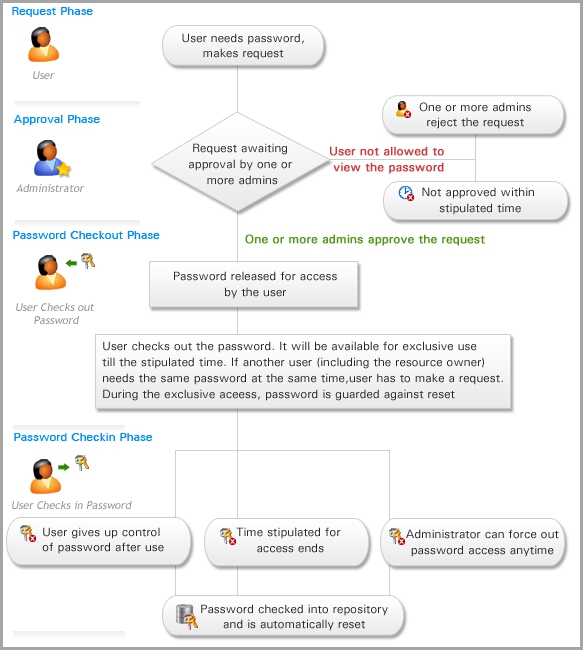
The SolutionOne of the effective ways to securely manage the administrative passwords is to store the passwords in a central, secure storage and automate password management tasks. Deploying 'Password Management Applications' or in simple words, the 'Enterprise Password Managers' can help organizations in controlling access to administrative passwords and in taking total control of the shared administrative passwords.
Password Manager Pro is a secure vault for storing and managing shared sensitive information such as passwords, documents and digital identities of enterprises. The benefits of deploying Password Manager Pro include:
- Eliminating password fatigue and security lapses by deploying a secure, centralized vault for password storage and access
- Improving IT productivity many times by automating frequent password changes required in critical systems
- Providing preventive & detective security controls through approval workflow & real-time alerts on password access
- Meeting security audits and regulatory compliance such as SOX, HIPAA and PCI



 In many production networks, it is not uncommon to find service accounts with 'static' credentials. Service accounts are normally forgotten after configuring them initially. Passwords are not changed for ages due to the sheer complexity of the service account password reset process. The new password has to be updated in all the associated services or processes. Otherwise, many services will simply not work. Unless the administrator follows the best practice of meticulously maintaining a master list of all service accounts and their dependencies/associations, password change of service accounts will prove herculean.
In many production networks, it is not uncommon to find service accounts with 'static' credentials. Service accounts are normally forgotten after configuring them initially. Passwords are not changed for ages due to the sheer complexity of the service account password reset process. The new password has to be updated in all the associated services or processes. Otherwise, many services will simply not work. Unless the administrator follows the best practice of meticulously maintaining a master list of all service accounts and their dependencies/associations, password change of service accounts will prove herculean. 
 Similarly, when there are too many IT resources, administrators often find it easier to assign a non-unique, same password to all the resources. Or they would prefer to recycle previously used passwords.
Similarly, when there are too many IT resources, administrators often find it easier to assign a non-unique, same password to all the resources. Or they would prefer to recycle previously used passwords.